這個(gè)消息從5月19日就傳開(kāi)了。可以理解為網(wǎng)絡(luò)戰(zhàn)的最新發(fā)展態(tài)勢(shì)——借由法律為名的公開(kāi)化。

From left, Chinese military officers Gu Chunhui, Huang Zhenyu, Sun Kailiang, Wang Dong, and Wen Xinyu have been indicted on cyber espionage charges.
美國(guó)司法部認(rèn)為有必要起訴的理由是認(rèn)為這個(gè)刺探行動(dòng)超越了他們“給自己劃定”的軍事、政治領(lǐng)域,而將刺探的信息用于經(jīng)濟(jì)目的。在起訴書(shū)中大量列舉了受害者的失竊信息,我猜想他們都應(yīng)該向FBI報(bào)案了。
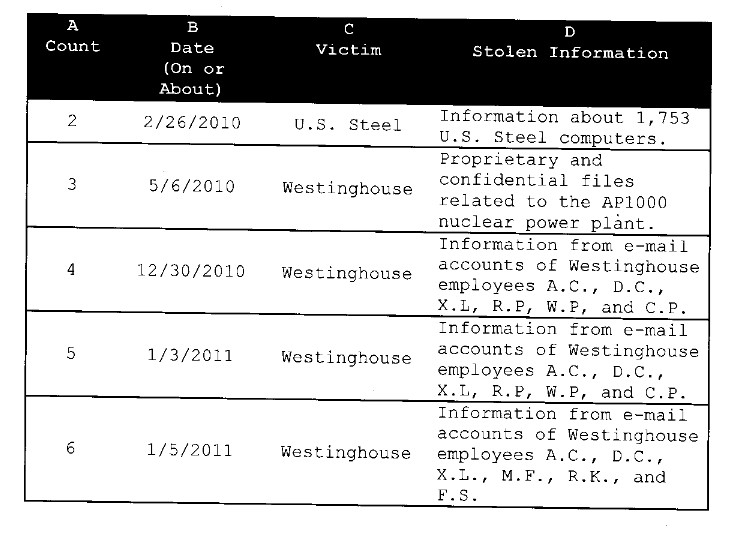
起碼,他們知道他們有什么信息被竊取了,并且通過(guò)手段找到了他們認(rèn)定的犯罪份子。單就這兩點(diǎn)而言,可見(jiàn)美國(guó)的信息與網(wǎng)絡(luò)安全取證的水平之高。
FBI的新聞稿中寫道:Wang Dong, Sun Kailiang, Wen Xinyu, Huang Zhenyu, and Gu Chunhui, who were officers in Unit 61398 of the Third Department of the Chinese People’s Liberation Army (PLA). The indictment alleges that Wang, Sun, and Wen, among others known and unknown to the grand jury, hacked or attempted to hack into U.S. entities named in the indictment, while Huang and Gu supported their conspiracy by, among other things, managing infrastructure (e.g., domain accounts) used for hacking.
受害人: Westinghouse Electric Co. (Westinghouse); U.S. subsidiaries of SolarWorld AG (SolarWorld); United States Steel Corp. (U.S. Steel); Allegheny Technologies Inc. (ATI); the United Steel, Paper and Forestry, Rubber, Manufacturing, Energy, Allied Industrial and Service Workers International Union (USW); and Alcoa Inc.
刺探的時(shí)間跨度: 2006-2014
31條犯罪指控: 31 counts as follow (all defendants are charged in all counts):
|
Count(s) |
Charge |
Statute |
Maximum Penalty |
|
One |
Conspiring to commit computer fraud and abuse
|
18 U.S.C. § 1030(b) |
10 years |
|
Two through nine |
Accessing (or attempting to access) a protected computer without authorization to obtain information for the purpose of commercial advantage and private financial gain |
18 U.S.C. §§ 1030(a)(2)(C), 1030(c)(2)(B)(i)-(iii), and 2 |
Five years (each count) |
|
10-23 |
Transmitting a program, information, code, or command with the intent to cause damage to protected computers |
18 U.S.C. §§ 1030(a)(5)(A), 1030(c)(4)(B), and 2 |
10 years (each count) |
|
24-29 |
Aggravated identity theft |
18 U.S.C. §§ 1028A(a)(1), (b), (c)(4), and 2 |
Two years (mandatory consecutive) |
|
30 |
Economic espionage |
18 U.S.C. §§ 1831(a)(2), (a)(4), and 2 |
15 years |
|
31 |
Trade secret theft |
18 U.S.C. §§ 1832(a)(2), (a)(4), and 2 |
10 years |
Summary of Defendants’ Conduct Alleged in the Indictment
|
Defendant |
Victim |
Criminal Conduct |
|
Sun |
Westinghouse |
In 2010, while Westinghouse was building four AP1000 power plants in China and negotiating other terms of the construction with a Chinese SOE (SOE-1), including technology transfers, Sun stole confidential and proprietary technical and design specifications for pipes, pipe supports, and pipe routing within the AP1000 plant buildings.
Additionally, in 2010 and 2011, while Westinghouse was exploring other business ventures with SOE-1, Sun stole sensitive, non-public, and deliberative e-mails belonging to senior decision-makers responsible for Westinghouse’s business relationship with SOE-1. |
|
Wen |
SolarWorld |
In 2012, at about the same time the Commerce Department found that Chinese solar product manufacturers had “dumped” products into U.S. markets at prices below fair value, Wen and at least one other, unidentified co-conspirator stole thousands of files including information about SolarWorld’s cash flow, manufacturing metrics, production line information, costs, and privileged attorney-client communications relating to ongoing trade litigation, among other things. Such information would have enabled a Chinese competitor to target SolarWorld’s business operations aggressively from a variety of angles. |
|
Wang and Sun |
U.S. Steel |
In 2010, U.S. Steel was participating in trade cases with Chinese steel companies, including one particular state-owned enterprise (SOE-2). Shortly before the scheduled release of a preliminary determination in one such litigation, Sun sent spearphishing e-mails to U.S. Steel employees, some of whom were in a division associated with the litigation. Some of these e-mails resulted in the installation of malware on U.S. Steel computers. Three days later, Wang stole hostnames and descriptions of U.S. Steel computers (including those that controlled physical access to company facilities and mobile device access to company networks). Wang thereafter took steps to identify and exploit vulnerable servers on that list. |
|
Wen |
ATI |
In 2012, ATI was engaged in a joint venture with SOE-2, competed with SOE-2, and was involved in a trade dispute with SOE-2. In April of that year, Wen gained access to ATI’s network and stole network credentials for virtually every ATI employee. |
|
Wen |
USW |
In 2012, USW was involved in public disputes over Chinese trade practices in at least two industries. At or about the time USW issued public statements regarding those trade disputes and related legislative proposals, Wen stole e-mails from senior USW employees containing sensitive, non-public, and deliberative information about USW strategies, including strategies related to pending trade disputes. USW’s computers continued to beacon to the conspiracy’s infrastructure until at least early 2013. |
|
Sun |
Alcoa |
About three weeks after Alcoa announced a partnership with a Chinese state-owned enterprise (SOE-3) in February 2008, Sun sent a spearphishing e-mail to Alcoa. Thereafter, in or about June 2008, unidentified individuals stole thousands of e-mail messages and attachments from Alcoa’s computers, including internal discussions concerning that transaction. |
|
Huang |
|
Huang facilitated hacking activities by registering and managing domain accounts that his co-conspirators used to hack into U.S. entities. Additionally, between 2006 and at least 2009, Unit 61398 assigned Huang to perform programming work for SOE-2, including the creation of a “secret” database designed to hold corporate “intelligence” about the iron and steel industries, including information about American companies. |
|
Gu |
|
Gu managed domain accounts used to facilitate hacking activities against American entities and also tested spear phishing e-mails in furtherance of the conspiracy. |
撇開(kāi)政治不談,我好奇的是他們的取證分析技術(shù)和方法。
根據(jù)指控書(shū)和相關(guān)材料顯示,有幾點(diǎn)比較有趣:
1)為何那么多起美國(guó)政府認(rèn)定的來(lái)自的攻擊都沒(méi)有起訴,偏偏這次起訴了呢?原因就在于他們這次認(rèn)定了攻擊行動(dòng)獲取的企業(yè)機(jī)密信息被用于了經(jīng)濟(jì)目的,并提供給了本國(guó)的企業(yè),用于獲得競(jìng)爭(zhēng)優(yōu)勢(shì)。那么,他們是如何具體闡述的呢?他們說(shuō),這個(gè)部隊(duì)的人一方面有組織地對(duì)美國(guó)企業(yè)進(jìn)行刺探,獲取機(jī)密情報(bào)信息,另一方面這個(gè)部隊(duì)的人也為國(guó)內(nèi)的企業(yè)提供安全服務(wù),在為客戶提供安全服務(wù)的時(shí)候,將之前獲取的信息透露給了這些國(guó)內(nèi)企業(yè)(主要是幾家SOE——國(guó)有企業(yè))。仔細(xì)一看,他們還真是分析的很深。
2)在認(rèn)定是這個(gè)部隊(duì)的人的時(shí)候,用了N種方法互相印證,我猜想用到了之前Mandiant的APT1報(bào)告中列舉的那些證據(jù)或者類似的、更高級(jí)的證據(jù)。同時(shí),他們還提到了一個(gè)論證,就是發(fā)現(xiàn)用于回傳機(jī)密數(shù)據(jù)的動(dòng)態(tài)DNS的網(wǎng)站的流量的周期性波動(dòng),具有顯著的早8點(diǎn)到晚5點(diǎn)(中國(guó)時(shí)間)的波峰特性,而其他時(shí)間(還有中午1個(gè)小時(shí))則呈現(xiàn)波谷,說(shuō)這跟中國(guó)國(guó)有事業(yè)單位的上班時(shí)間很吻合。在指控書(shū)附錄中還貼出了幾幅流量圖。很有意思。
3)在指控書(shū)中還比較詳細(xì)的枚舉了受害人失竊的信息,細(xì)到了具體的主機(jī)名,信息類型,甚至個(gè)別條目。
看了這些你就明白為什么FireEye要收購(gòu)Mandiant,檢測(cè)威脅很重要,數(shù)字取證分析和溯源也很重要啊!結(jié)合到一起才NB。









